Nonprofit Resources
Remote Desktop Protocol (RDP): Balancing Convenience with Security
Yet while RDP provides convenience and efficiency to many organizations, it also has many security implications. It’s too useful to give up, but is it too dangerous to keep? Before we can evaluate the solutions for securing this type of remote access, we need to understand what RDP is and why it has become a popular target for cyber criminals.
The History of RDP
Microsoft created RDP over 20 years ago and it has been widely adopted for its simple graphical interface and ease of use when connecting to other computers. The protocol is built into the majority of Windows operating systems as a server, and the client required for access is available on most operating systems, including Windows, macOS, UNIX, and Linux. As a result, RDP provides the ability for a user to remote into another computer via a known port from anywhere, with hardly any setup on the user side.
Third-party software that allows a user to remote into another computer has since been introduced, including LogMeIn, TeamViewer, and join.me. While this software offers more features than a regular RDP client, the use of RDP — which is built into existing systems and free — has not declined. RDP continues to be easy and cost-effective for organizations.
In September 2018, the FBI’s Internet Crime Complaint Center (IC3) released an announcement about cyber criminals increasingly exploiting RDP and ongoing attacks against devices with the port open to the Internet. IC3 encouraged organizations to evaluate their use of RDP and the controls in place to secure it.
As noted above, RDP is not a new service. So how is it still being so heavily exploited after its initial release?
RDP Exploits
As with any piece of software, bugs arise sooner or later. A critical security exploit allowing a man-in-the-middle-style attack was discovered in RDP version 5.2. In 2012, another critical vulnerability was discovered to allow a Windows computer to be compromised by unauthenticated clients. Version 6.1, found in Windows Server 2008, revealed a critical exploit that harvested user credentials. And more recently, an exploit discovered in March 2018 allowed remote code execution attack and another credential-harvesting scenario.
At the same time, hackers are well aware of the extensive use of RDP within organizations. As a result, they are now targeting RDP as a method to proliferate their attacks. The evolution of ransomware is a prime example. Ransomware has proven to be a very lucrative form of cyber attack, and hackers have begun to target RDP to spread this form of malware within organizations.
Similarly, capturing and selling RDP credentials on the dark web has also proven to be a money-making scheme for hackers. RDP credentials sell on dark markets for about $3 apiece, on average. One set of credentials allows you complete control via RDP, and some dark web sites have thousands of compromised credentials for sale.
Human error has also contributed to the exploitation of RDP. Overworked, stressed, or novice network administrators often feel that they need to respond quickly to users seeking an easy and efficient method of remote access. Since RDP is built into operating systems, many network administrators failed to consider the implications of exposing RDP to the public Internet. And once third-party software became the norm, RDP became a backup solution and an afterthought. It was essentially out of sight, out of mind.
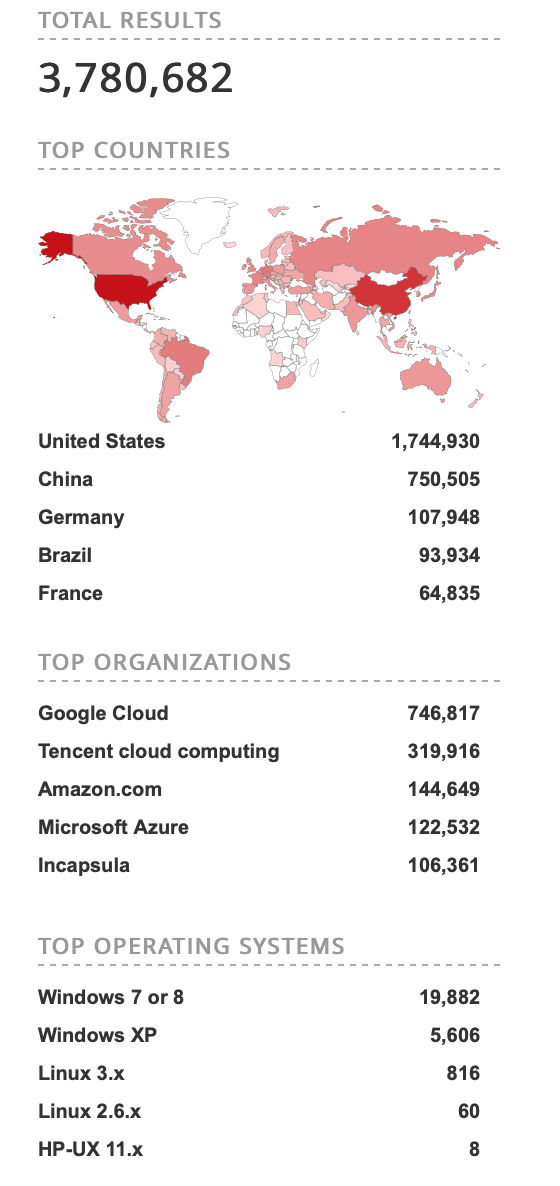
At this point, the risk associated with RDP sessions is inarguable, but RDP usage hasn’t declined. On the contrary, it has increased rapidly as more organizations use remote locations, rely on cloud computing, and decrease the use of physical hardware with emerging technologies such as virtualization. A query on Shodan, a search engine used to scan specific types of computers that populate the entire Internet, shows just how extensively RDP is used. This screen capture, taken in January 2019, is a real-time view of how many computers have the default RDP port (port 3389) active and open for attack on the Internet.
How to Secure RDP
Until Microsoft disables the RDP client-server feature in all past, current, and future iterations of the Windows operating system, RDP will always be used. The macOS operating system also uses Microsoft’s branded RDP client. And with the release of Microsoft’s new HTML5 version of the RDP client, it is now entirely browser-based. This form of remote access is too convenient to discontinue fully. So what do we do?
Fortunately, you can secure RDP through layered controls. While this list is not exhaustive, it provides some basic guidelines for securing RDP in your organization:
- Disable any RDP connection to the open Internet. If nothing else, this will reduce the risk of hackers scanning your network and limit your susceptibility to brute force attacks.
- Change the default listening port from 3389.
- Update and apply patches regularly.
- Enable complex passwords and a conservative account lockout policy. Consider customizing a more stringent policy for RDP.
- Configure multi-factor authentication (MFA).
- Limit and reduce access via RDP and consider disabling all administrative access via RDP.
- Enable logging and monitoring capabilities to alert personnel of suspicious activity.
- Ensure self-signed certificates are in place.
- Enable the following on workstations and servers that use RDP:
- Network Level Authentication
- TLS 1.2
- FIPS compliance
While it may be difficult to stop using RDP, it’s crucial to take steps to secure it. Please contact us at [email protected] with any questions.
This article was originally published in The Nonprofit Times.

Allison Davis Ward
Allison Davis Ward is a Partner at CapinTech. Throughout her time as an information systems auditor and senior manager, Allison has provided information security assessment and consulting services primarily for nonprofit organizations, financial institutions, and health facilities. In addition to these services, she has provided clients with consulting services in risk assessment and policy development engagements.
